Came in this morning to a lovely issue, ADFS authenticated services were completely unavailable! Office 365 archive mailboxes, hosted CRM, etc.
Upon testing the URL: /adfs/services/trust/mex a lovely “Error 503” was displayed!

I changed the internal ADFS certs to use the new EKU requirements (Server and Client Authentication), verified NT SERVICE\drs and NT SERVICE\adfssrv had the correct permissions on the private keys, but still no dice for external usage.
After using my trusty bing.com, I came across this lovely Microsoft article about the KeySpec property for the Web Application Proxy server: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/technical-reference/ad-fs-and-keyspec-property
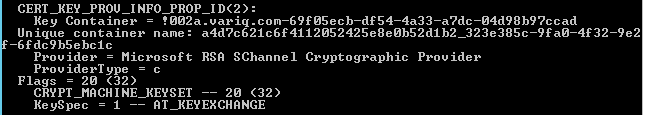
Checking the server’s keys using the Powershell command dir cert:/LocalMachine/My reveals the following problem:
KeySpec = 0

Ok, so the fix is easy right? Just export the cert to a pfx file, import it with
certutil -csp "Microsoft RSA SChannel Cryptographic Provider" -importpfx
or as the article says:
certutil –importpfx extcert.pfx AT_KEYEXCHANGE
In this case, I got a lovely -importPFX command FAILED: 0x80090029 The requested operation is not supported. error message as shown:

After looking around for a while, I remembered the article I wrote back in September 2017: LS Audio/Video Authentication Server Error 19008 – Private Key not found, went through that process, and what do you know, it worked!!
The URL: /adfs/services/trust/mex now works perfectly, and all services that depend on ADFS are up!
