Conditional Access
Now that we’ve gone over some a couple basics, I wanted to go through some of the features Azure AD has built in which not only blow on-premise AD away, but also show why a push to utilize it over it’s predecessor is vital for the modern workspace.
The modern security perimeter now extends beyond an organization’s network to include user and device identity. Organizations can use identity-driven signals as part of their access control decisions.
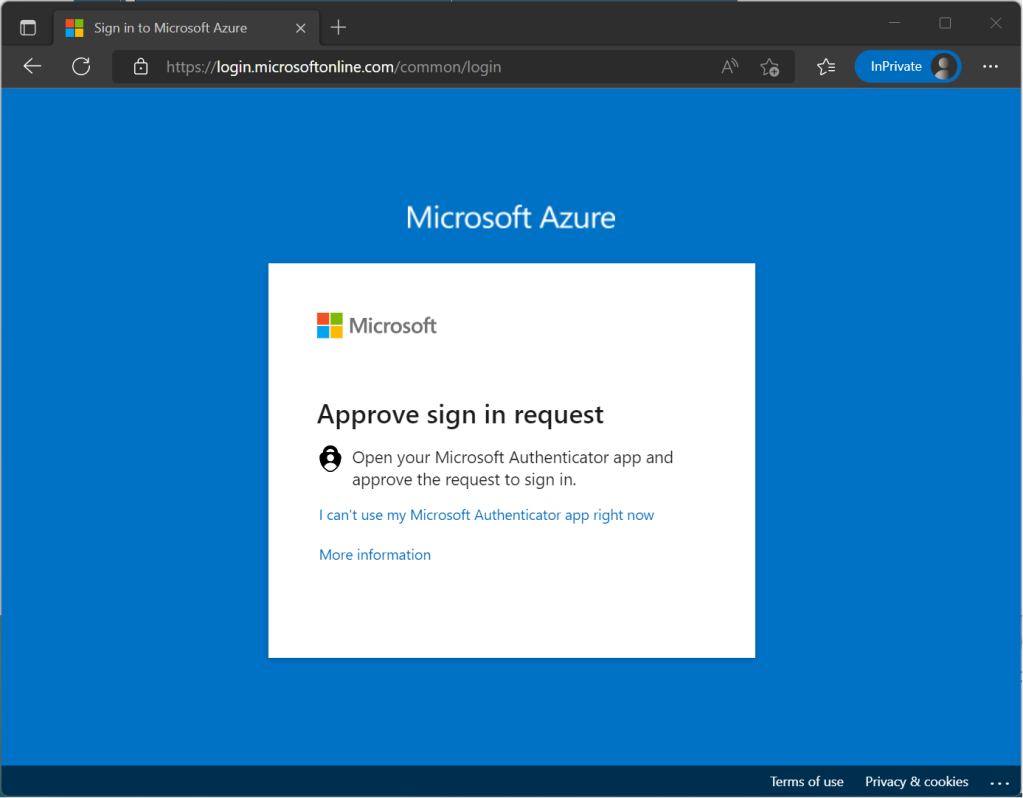
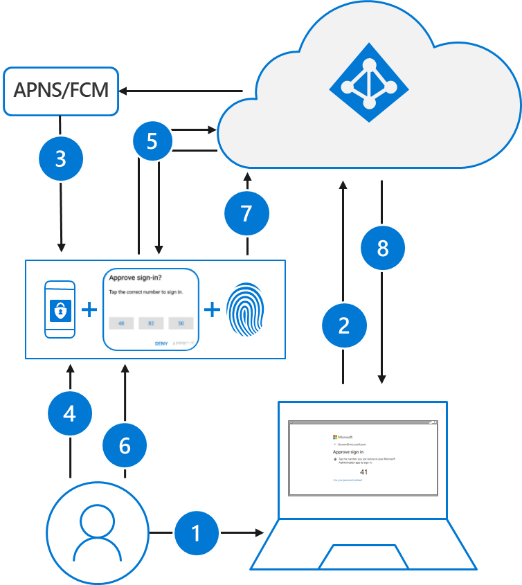
Conditional Access brings signals together, to make decisions, and enforce organizational policies. Azure AD Conditional Access is at the heart of the new identity-driven control plane.

I’ve especially seen post-Covid, with the workspace being more dispersed, the two goals I see most commonly requested are to:
- Empower users to be productive wherever and whenever
- Protect the organization’s assets
In my opinion, using Azure AD Conditional Access policies to apply the right access controls when needed is one of the strongest controls available for keeping the organization secure.
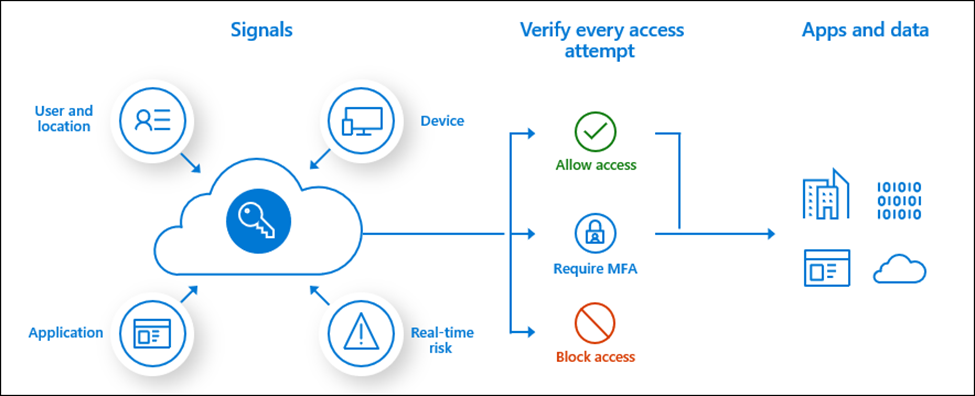
Signals that Conditional Access can use when making decisions include:
- User or group memberships
- Note: Dynamic memberships are super powerful here, drastically lowering the support overhead with utilizing this control!
- IP Location info
- Specific Device
- Based on application
- A.I. – like, by using real-time and calculated risk detection
- Note: This one is cool, as integration with AzAD Identity Protection allows the identity of risky sign-in behavior, and you can then force users to go through some of the options talked about in Part 1
Conditional Access is very powerful, however, I would recommend that it initially be implemented in “report only” mode. – Thankfully, for many obvious reasons, an excellent option.
Entitlement Management
Continuing in the same theme, either static, or automatic assignments of access packages can be created in Entitlement Management, which now include multi-stage reviews.
Access reviews can be built in sequential stages, each with their own set of reviewers and configurations, making it easy to design more efficient reviews for the resource owners and auditors by reducing the number of decisions each reviewer is accountable for.
Note: In the following sample, I have a third party application added as “Application”, the reason it shows up is because it is an Enterprise App registered in my Azure tenant, one can only imagine the possibilities here!

Up to three stages can be specified, in addition, you can define whether earlier stage decisions should be revealed to later-stage reviewers.
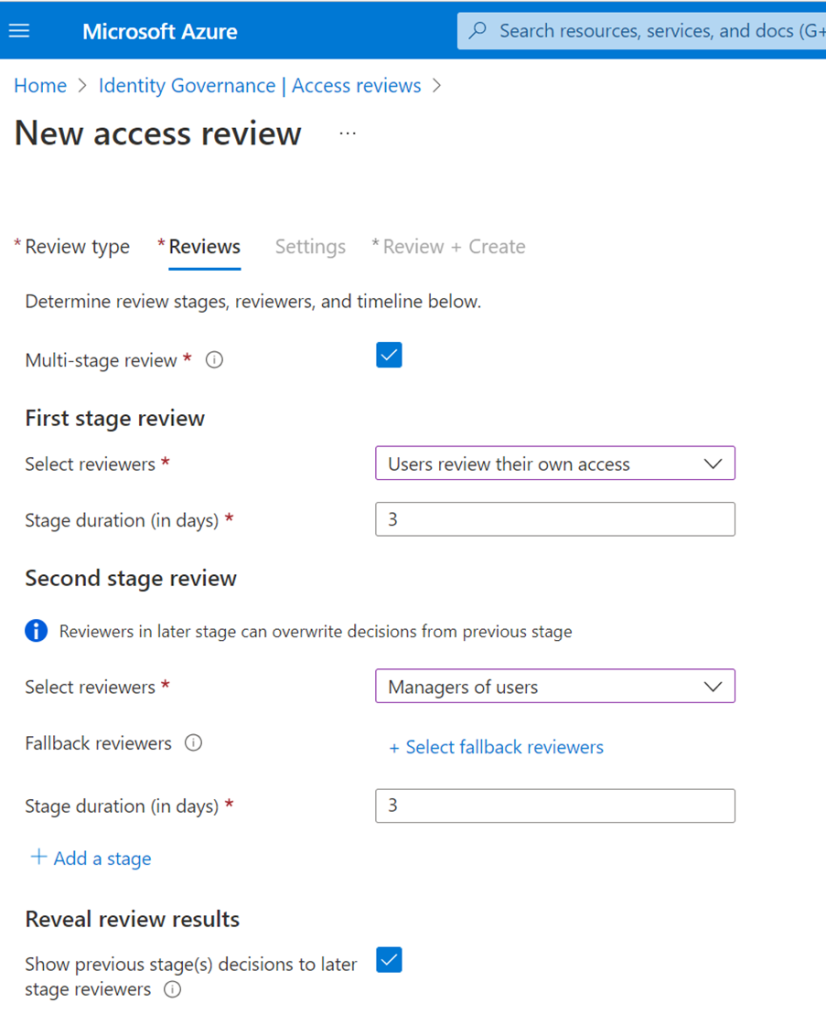
Automatic assignment of access policies
Azure AD now adds and removes users’ access across groups, Teams, SharePoint sites, and applications as their attributes change (such as when someone joins, moves between departments, etc.). The inclusion of this policy in an access package simplifies managing at scale; users don’t need to make requests, which not only ensures their access doesn’t remain longer than necessary, but also does so without the need for administrative interaction when someone moves teams.
Here’s a screenshot example for a policy I’ve got
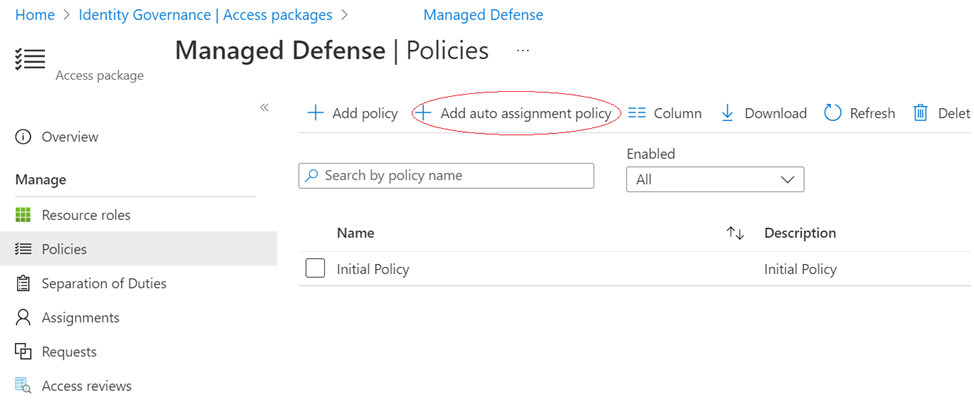
In this example, the rule is based on the attributes of the user, in this case department. Azure AD will automatically begin creating resource assignments for those users who meet the rule, without the need to request.

In addition to what be done with dynamic groups, we can also use entitlement management with automatic assignment policies for:
- Managing access across multiple resources, including applications, SharePoint Online sites, existing Azure AD groups and Teams, and groups that are provisioned to on-premises AD.
- Managing access with a combination of policies to have both rules (for instance, members in a department) and exceptions so that the exceptions can be regularly reviewed and removed, if no longer needed
- More automation of tasks across applications through entitlement management’s custom extensions, by running workflows when users receive or lose assignments